OS X has a netstat command, but it doesn't display information about the programs associated with the network connections. If you want to see that, you need to use lsof instead. Note that it must be run as root (i.e. With sudo) in order to see other users' programs. Sudo lsof -i lsof also has many options for controlling what's displayed. Sudo lsof -i tcp -nP # show TCP unly (no UDP),. PRTG Network Monitor. An advanced network monitoring solution to monitor network up/downtime.

Netstat — derived from the words network and statistics — is a program that's controlled via commands issued in the command line. It delivers basic statistics on all network activities and informs users on which portsand addresses the corresponding connections (TCP, UDP) are running and which ports are open for tasks. In 1983, netstat was first implemented into the Unix derivative BSD (Berkley Software Distribution), whose version 4.2 supported the first internet protocol family, TCP/IP. netstat has been integrated into Linux since its debut in 1991 and has been present in Windows since the appearance of version 3.11 (1993), which could also communicate via TCP/IP with the help of extensions. While the parameters of netstat's commands (as well as their outputs) differ from system to system, when it comes to their functions, the various implementations are very similar.
Ports, Processes, and Protocols. Network sockets can either be connected or waiting for a. Show Server Port and Process ID in Netstat Mac. Instead of netstat you need to use LSOF (lists open files and sockets), piped into grep which will only shows lines with LISTEN in them: sudo lsof -Pnl +M -i grep LISTEN. Use -i4 for ip4 and -i6 for ip6.i seems to work for all internet traffic. Handy for tracking down what program is running a.
Essentially, netstat is a command line program and for this reason doesn't feature a graphical user interface. Programs like TCPView, which was developed by the Microsoft division Windows Sysinternals, makes it possible for statistics to be displayed graphically.
How do you use netstat?
In Windows operating systems, you can use the netstat services via the command line (cmd.exe). You can find them in the start menu under 'All Programs' -> 'Accessories' -> 'Command Prompt'. Alternatively, you can search directly for 'Command Prompt' in the start menu's search field or start the command line via 'Run' (Windows key + press 'R' and enter 'cmd'). The syntax of the netstat commands follows the following pattern:
The combination of the individual options works by stringing the individual parameters together, each separated by a space:
The parameters are typically preceded by a hyphen (-), but if you want to combine several options, you only have to place this hyphen in front of the first element. Instead of the variant shown above, you can also link different parameters as follows:
In this case, it is important that you do not leave any spaces between the individual netstat options.
netstat commands for Windows
[OPTION] | Command | Description |
netstat | Standard listing of all active connections | |
-a | netstat -a | Displays all active ports |
-b | netstat -b | Displays the executable file of a connection or listening port (requires administrator rights) |
-e | netstat -e | Shows statistics about your network connection (received and sent data packets, etc.) |
-f | netstat -f | Displays the fully qualified domain name (FQDN) of remote addresses |
-i | netstat -i | Brings up the netstat overview menu |
-n | netstat -n | Numerical display of addresses and port numbers |
-o | netstat -o | Displays the process identifier (PID) associated with each displayed connection |
-p Protokoll | netstat -p TCP | Displays the connections for the specified protocol, in this case TCP (also possible: UDP, TCPv6, or UDPv6) |
-q | netstat -q | Lists all connections, all listening TCP ports, and all open TCP ports that are not listening |
-r | netstat -r | Displays the IP routing table |
-s | netstat -s | Retrieves statistics about the important network protocols such as TCP, IP, or UDP |
-t | netstat -t | Shows the download status (TCP download to relieve the main processor) of active connections |
-x | netstat -x | Informs about all connections, listeners, and shared endpoints for NetworkDirect |
-y | netstat -y | Displays which connection templates were used for the active TCP connections |
Interval | netstat -p 10 | Displays the respective statistics again after a selected number of seconds (here 10); can be combined as required (here with –p), [CTRL] + [C] ends the interval display |
Netstat examples
In order to make the use of the listed netstat commands for Windows easier to understand, we will show you some example commands:
List of all connections for the IPv4 protocol
If you don't want to retrieve all active connections, but only all active IPv4 connections, you can do this using the netstat command:
Accessing statistics using the ICMPv6 protocol
If you only want to obtain statistics on the ICMPv6 protocol, enter the following command in the command line:
Repetitive query of interface statistics (every 20 seconds)
Use the following netstat command for a repeated query of the interface statistics, which returns new values every 20 seconds on received and sent data packets:
Display of all open ports and active connections (numeric and process ID included)
One of the most popular netstat commands is undoubtedly to query all open ports and active connections (including process ID) in numeric form:
Why using netstat makes sense


When dealing with excessive traffic and malicious software it's advantageous to be informed about the inbound and outbound connections to your computer. These are created via their respective network addresses that indicate which ports were preemptively opened for exchanging data. Once a port is opened, it receives the status 'LISTEN' and waits for connection attempts. One problem of having these ports remain open is that your system is then left vulnerable to malware. What's more, there's also a chance that Trojan viruses already found in your system may install a backdoor, opening up a corresponding port in the process. For this reason, you should always regularly check the ports opened by your system, a task for which netstat is particularly well suited. Thanks to the fact that you'll be able to find the diagnosis tool on virtually every system, whether it be Unix, Linux, Windows, or Mac, this program offers a unified solution for all computers and servers.

Netstat — derived from the words network and statistics — is a program that's controlled via commands issued in the command line. It delivers basic statistics on all network activities and informs users on which portsand addresses the corresponding connections (TCP, UDP) are running and which ports are open for tasks. In 1983, netstat was first implemented into the Unix derivative BSD (Berkley Software Distribution), whose version 4.2 supported the first internet protocol family, TCP/IP. netstat has been integrated into Linux since its debut in 1991 and has been present in Windows since the appearance of version 3.11 (1993), which could also communicate via TCP/IP with the help of extensions. While the parameters of netstat's commands (as well as their outputs) differ from system to system, when it comes to their functions, the various implementations are very similar.
Ports, Processes, and Protocols. Network sockets can either be connected or waiting for a. Show Server Port and Process ID in Netstat Mac. Instead of netstat you need to use LSOF (lists open files and sockets), piped into grep which will only shows lines with LISTEN in them: sudo lsof -Pnl +M -i grep LISTEN. Use -i4 for ip4 and -i6 for ip6.i seems to work for all internet traffic. Handy for tracking down what program is running a.
Essentially, netstat is a command line program and for this reason doesn't feature a graphical user interface. Programs like TCPView, which was developed by the Microsoft division Windows Sysinternals, makes it possible for statistics to be displayed graphically.
How do you use netstat?
In Windows operating systems, you can use the netstat services via the command line (cmd.exe). You can find them in the start menu under 'All Programs' -> 'Accessories' -> 'Command Prompt'. Alternatively, you can search directly for 'Command Prompt' in the start menu's search field or start the command line via 'Run' (Windows key + press 'R' and enter 'cmd'). The syntax of the netstat commands follows the following pattern:
The combination of the individual options works by stringing the individual parameters together, each separated by a space:
The parameters are typically preceded by a hyphen (-), but if you want to combine several options, you only have to place this hyphen in front of the first element. Instead of the variant shown above, you can also link different parameters as follows:
In this case, it is important that you do not leave any spaces between the individual netstat options.
netstat commands for Windows
[OPTION] | Command | Description |
netstat | Standard listing of all active connections | |
-a | netstat -a | Displays all active ports |
-b | netstat -b | Displays the executable file of a connection or listening port (requires administrator rights) |
-e | netstat -e | Shows statistics about your network connection (received and sent data packets, etc.) |
-f | netstat -f | Displays the fully qualified domain name (FQDN) of remote addresses |
-i | netstat -i | Brings up the netstat overview menu |
-n | netstat -n | Numerical display of addresses and port numbers |
-o | netstat -o | Displays the process identifier (PID) associated with each displayed connection |
-p Protokoll | netstat -p TCP | Displays the connections for the specified protocol, in this case TCP (also possible: UDP, TCPv6, or UDPv6) |
-q | netstat -q | Lists all connections, all listening TCP ports, and all open TCP ports that are not listening |
-r | netstat -r | Displays the IP routing table |
-s | netstat -s | Retrieves statistics about the important network protocols such as TCP, IP, or UDP |
-t | netstat -t | Shows the download status (TCP download to relieve the main processor) of active connections |
-x | netstat -x | Informs about all connections, listeners, and shared endpoints for NetworkDirect |
-y | netstat -y | Displays which connection templates were used for the active TCP connections |
Interval | netstat -p 10 | Displays the respective statistics again after a selected number of seconds (here 10); can be combined as required (here with –p), [CTRL] + [C] ends the interval display |
Netstat examples
In order to make the use of the listed netstat commands for Windows easier to understand, we will show you some example commands:
List of all connections for the IPv4 protocol
If you don't want to retrieve all active connections, but only all active IPv4 connections, you can do this using the netstat command:
Accessing statistics using the ICMPv6 protocol
If you only want to obtain statistics on the ICMPv6 protocol, enter the following command in the command line:
Repetitive query of interface statistics (every 20 seconds)
Use the following netstat command for a repeated query of the interface statistics, which returns new values every 20 seconds on received and sent data packets:
Display of all open ports and active connections (numeric and process ID included)
One of the most popular netstat commands is undoubtedly to query all open ports and active connections (including process ID) in numeric form:
Why using netstat makes sense
When dealing with excessive traffic and malicious software it's advantageous to be informed about the inbound and outbound connections to your computer. These are created via their respective network addresses that indicate which ports were preemptively opened for exchanging data. Once a port is opened, it receives the status 'LISTEN' and waits for connection attempts. One problem of having these ports remain open is that your system is then left vulnerable to malware. What's more, there's also a chance that Trojan viruses already found in your system may install a backdoor, opening up a corresponding port in the process. For this reason, you should always regularly check the ports opened by your system, a task for which netstat is particularly well suited. Thanks to the fact that you'll be able to find the diagnosis tool on virtually every system, whether it be Unix, Linux, Windows, or Mac, this program offers a unified solution for all computers and servers.
Possible infections can be caught based on unknown opened ports or unknown IP addresses. In order to obtain an informative result, all other programs, such as your internet browser, should be turned off. This is due to the fact that these are often connected with computers that possess unknown IP addresses. Thanks to the detailed statistics, users also receive information on the packets that have been transferred since the last system start as well as notices of any errors that have occurred. The routing table, which delivers information on the paths data packets takes through the net, can be displayed with the help of the system-specific netstat command.
Related articlesNetstat Tool For Mac
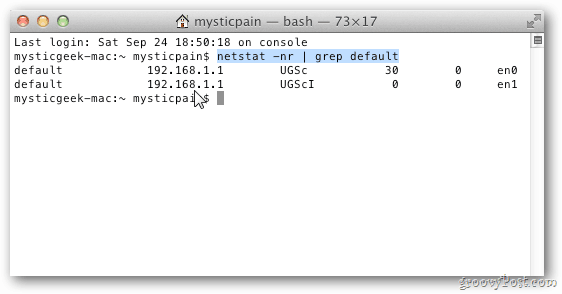
I've recently switched from Linux to Mac OS X and I'm trying to get used to the new environment. One of the differences from Linux is the way to find the process id (pid) listening on a specific port. In Linux you do like this:
to show the pid listening on port 8080. On Max OS X how ever you'll run into the following error message:
The way to find the pid on the Mac is to do like this:
which will give us:
Mac Os Check Port Usage
java 4582 johan 194u IPv6 0x1de155f6b2c74d03 0t0 TCP *:websm (LISTEN)
where 4582 is the pid listening on port 8080. The problem, for me at least, is that this is not a trivial command to remember. To make it simpler I wanted to add it as an alias in .bash_profile in my home directory. The problem now is that aliases won't accept parameters the same way that bash scripts does (by using $@). This is actually not a problem if parameters should be added to the end of an alias. For example consider the following alias:
List Open Ports Mac
We've now aliased grep to be case-insensitive so when running for example
Netstat Command For Mac
we can find the folder called foldername
But in our case the port parameter should not be appended at the end of our alias. So what we have to do to get around this is to first wrap the command in a function and then create an alias to that function:
You can now use pidport 8080 to find the pid of the process listening on port 8080. Prefix lsof with sudo to see process ids that you don't own.
